Cryptography in Blockchain
Apr 29, 2022 By Puneet vermaContents
- 1. Introduction
- 2. Properties
- 3. Common terms in cryptographic
- 4. Type of cryptography
- 5. How do we achieve confidentiality?
- 6. How do we achieve authentication?
- 7. Achieve both confidentiality and authentication
- 8 .Hash Function vs cryptographic Hash Function
- 9. Hashing vs Encrption
- 10. Cryptography in Blockchain
Cryptography is the method of securing data from unauthorised access. When we say Cryptography, we are looking for the following.
Before going to blockchain in cryptography, let's first understand cryptography.
Confidentiality
The information cannot be understood by anyone for whom it was unintended. Except for the sender and receiver, no one can read the message.
Integrity
Integrity is used to ensure that nobody in between the sender and receiver can change some parts of the message.
Non-repudiation
The sender can't deny that he has not sent that message at a later stage.
Authentication
To verify the identity of who created the message.
Commons terms in cryptographic
Encryption: It is a process of converting plaintext to ciphertext.
Decryption: It is a process of converting ciphertext to plaintext.
Cipher: It is the unreadable output of an encryption algorithm.
Key: A key is a piece of information. Usually, a string of numbers or letters, which, when processed through a cryptographic algorithm, can encode or decode cryptographic data.
Type of cryptography
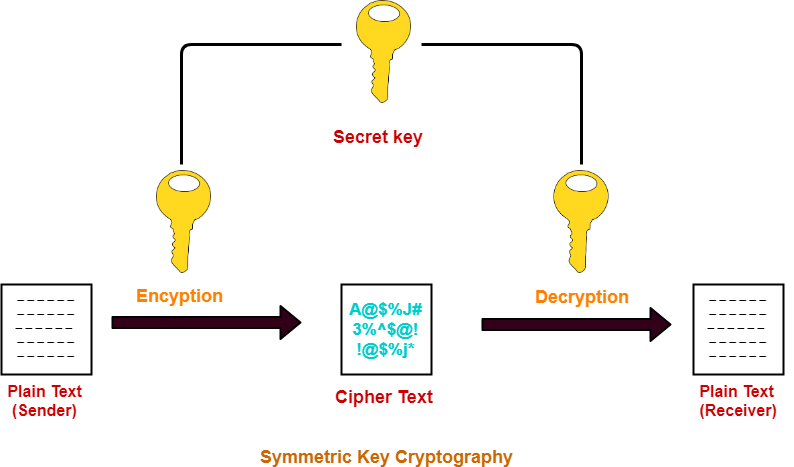
Symmetric key cryptography
It uses the same key to encrypt and decrypt information.
Asymmetric key cryptography
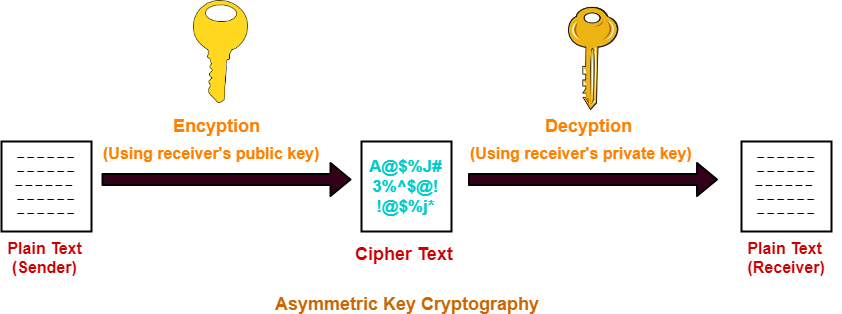
In asymmetric cryptography, we have a pair of public and private keys. The public key is used to encrypt the data, while the private key decrypts the data.
The public key is known to everybody, while the private key is secret.
Whoever wants to send a message to any receiver uses the receiver's public key to encrypt the data, and the receiver uses its private key to decrypt the data.
How do we achieve confidentiality?
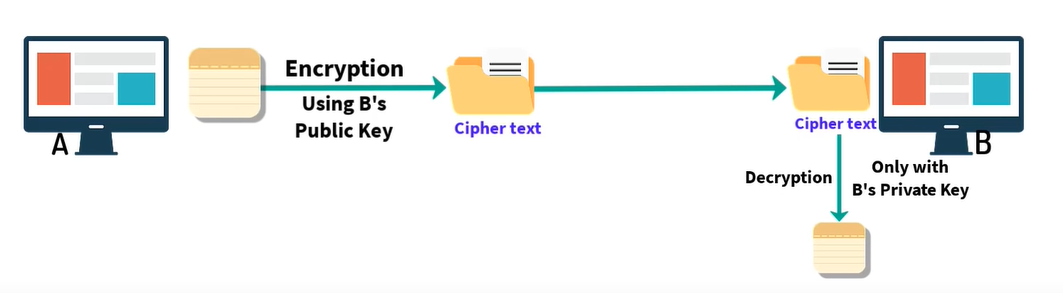
Anyone can send a message to B by using B's public, But only B can read that message using its private key.
How do we achieve authentication?
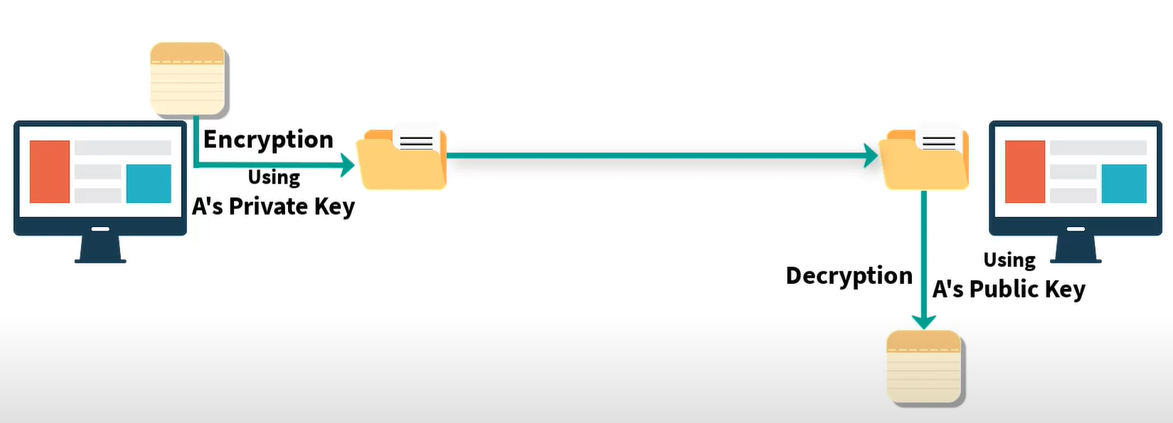
Suppose the sender uses his private key and encrypts the message if the receiver can decrypt the message with A's public key. That means the information came from A. This is called Digital Signature.
But the problem is that everybody has A's public and can decrypt the message. This breaks confidentiality.
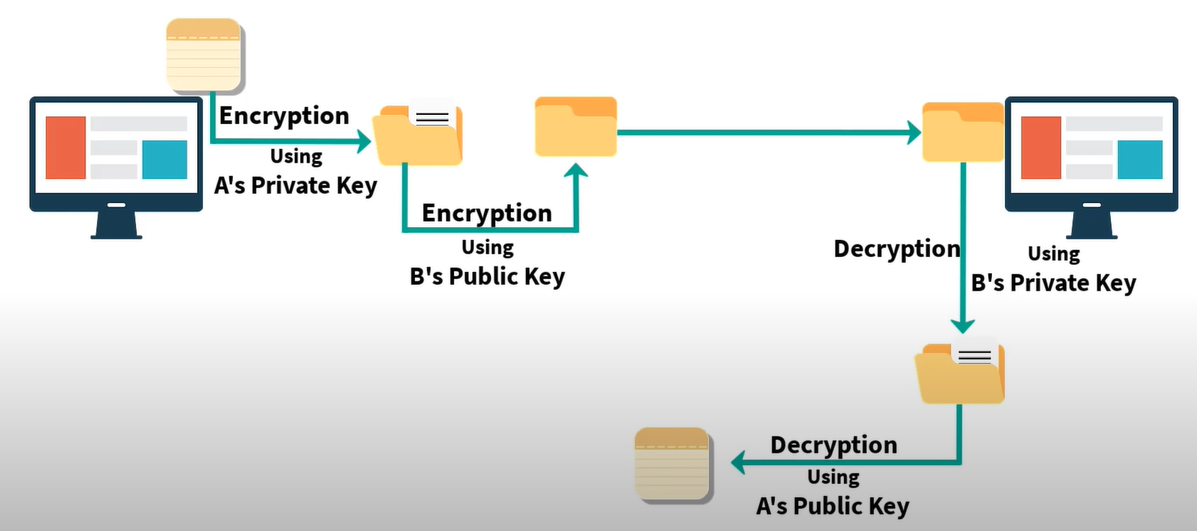
How do we achieve both confidentiality and authentication?
This is a fascinating setup, where A will use his private key to encrypt the data, and then A will use B's Public key to encrypt it again.
On the receiver end, B will first use his private key to decrypt the. This gives confidentiality. Then B will use A's public key to once again decrypt the data, and this is the way we achieve authentication.
What is the difference between a Hash Function and a Cryptographic Hash Function?
- Every cryptographic hash function is a hash function. But not every hash function is a cryptographic hash.
- Concept-wise, they are the same,
- We consider a hash function as a cryptographic hash function when it hard to find collisions or pre-images
Case Study MD5 is broken.
Earlier, MD5 was considered a cryptographic hash function, but in 2008, we found that we could easily find collisions. We should not use MD5, as it is less secure.
Read more
Hashing vs Encrption
- Encryption is a two-way function that includes encryption and decryption, while hashing is a one-way function that changes a plain text to an irreversible unique digest.
- Hashing is used to validate the integrity. While encryption encodes data for the primary purpose of maintaining data confidentiality and security. It requires a private key to decrypt.
- They are similar in the sense that they both transform data into a different format.
Cryptography in Blockchain
Blockchains make use of two types of cryptographic algorithms,
- Asymmetric key
- Hash functions generally SHA-256
Asymmetric key
The public key, visible globally, is used as the person's address, while the private key is a secret used to access or perform any actions on that address data.
Hash function
Hash is used in the chain part of a blockchain. The hash value of that block is used as an address of that block. Any alteration in the block data can lead to inconsistency and break the blockchain, making it invalid.